For this post we want to focus on capturing and analyzing traffic on DLS2 fa0/18 VLAN 10 that connects to PCC. In essence, we want to monitor the traffic to and from PCC using RSPAN (Remote Switched Port Analyzer). SRV will monitor the traffic using Wireshark. For the end test we will send a ping from PCB to PCC and see the ICMP packets on SRV running Wireshark.
Configurations:
VTP: DLS1, DLS2, ALS1 in domain ccnp.net and set to transparent mode.
SRV: 10.1.50.1 – static DGW: 10.1.50.254
PCB: DHCP DGW: 10.1.20.254
PCC: DHCP DGW: 10.1.10.254
Po1: dot1q trunk
Po2: dot1q trunk
DLS1: HSRP (10.1.x.252/24) active for vlan’s 5, 20 (where x is the vlan number)
DLS2: HSRP (10.1.x.253/24) active for vlan’s 10, 50 (where x is the vlan number)
DHCP Pool VLAN 10:
Excluded addresses: 10.1.10.252 – 10.1.10.254
Default Gateway 10.1.10.254
Domain ccnp.netDHCP Pool VLAN 20
Excluded addresses: 10.1.20.252 – 10.1.20.254
Default Gateway 10.1.20.254
We have connectivity throughout: PCB, PCC & SRV can all ping each other.
To set up RSPAN we need to have a source to monitor… which is fa0/18 on DLS2 (DLS2 to PCC). If the analyzer was local we could just use SPAN but since the analyzer (Wireshark on SRV) is not local we will use RSPAN and need to set up a destination. To do this we need to create a new vlan and set it as a remote-span.
We will start at the source first and work our way back to the analyzer (SRV).
On DLS2:
DLS2(config)# vlan 77
DLS2(config-vlan)# name RSPAN
DLS2(config-vlan)# remote-span
DLS2(config-vlan)# exit
DLS2(config)# monitor session 1 source inter fa0/18 ?
, Specify another range of interfaces
- Specify a range of interfaces
both Monitor received and transmitted traffic
rx Monitor received traffic only
tx Monitor transmitted traffic only
<cr>
NOTE: ‘both’ or “Monitor received and transmitted traffic” is the default so there is no need to add this.
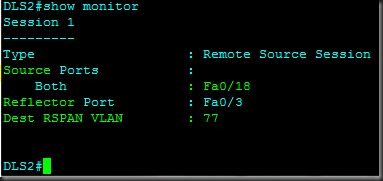
DLS2(config)#monitor session 1 source inter fa0/18
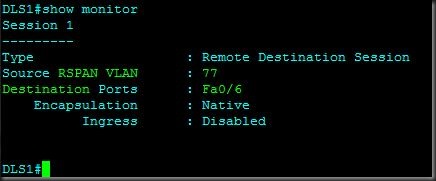
DLS2(config)#monitor session 1 destination remote vlan 77 reflector-port fa0/3
Here we configured the source and destination on DLS2. To configure the destination (the path to where the analyzer is located) over multiple hops we need to set vlan 77 as the ‘means’ to the ‘remote’ analyzer and the path to take from DLS2 is fa0/3. In other words, DLS2 should monitor fa0/18 and send that information out fa0/3 via vlan 77.
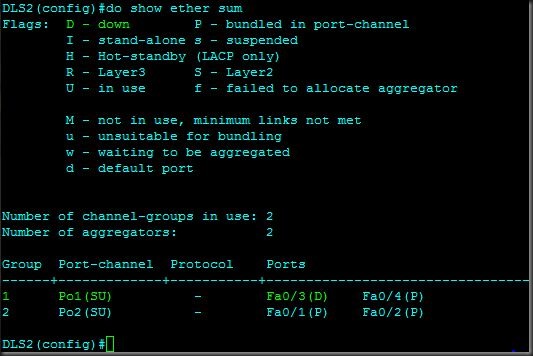
Note: A destination RSPAN (or SPAN) port cannot be an Etherchannel so this will take fa0/3 out of port-channel 1:
DLS1:
DLS1(config)#vlan 77
DLS1(config-vlan)#name RSPAN
DLS1(config-vlan)#remote-span
DLS1(config-vlan)#exit
DLS1(config)#monitor session 1 source remote vlan 77
DLS1(config)#monitor session 1 destination inter fa0/6
Going back to what can and cannot be a source or destination port, Cisco offers this (1):
A source port has these characteristics:
•It can be any port type (for example, EtherChannel, Fast Ethernet, Gigabit Ethernet, and so forth).
•It can be monitored in multiple SPAN sessions.
•It cannot be a destination port.
•Each source port can be configured with a direction (ingress, egress, or both) to monitor. For EtherChannel sources, the monitored direction would apply to all the physical ports in the group.
•Source ports can be in the same or different VLANs.
•For VLAN SPAN sources, all active ports in the source VLAN are included as source ports.
The destination port has these characteristics:
•It must reside on the same switch as the source port (for a local SPAN session).
•It can be any Ethernet physical port.
•It can participate in only one SPAN session at a time (a destination port in one SPAN session cannot be a destination port for a second SPAN session).
•It cannot be a source port or a reflector port.
•It cannot be an EtherChannel group or a VLAN.
•It can be a physical port that is assigned to an EtherChannel group, even if the EtherChannel group has been specified as a SPAN source. The port is removed from the group while it is configured as a SPAN destination port.
•The port does not transmit any traffic except that required for the SPAN session.
•If ingress traffic forwarding is enabled for a network security device, the destination port forwards traffic at Layer 2.
•It does not participate in spanning tree while the SPAN session is active.
•When it is a destination port, it does not participate in any of the Layer 2 protocols (STP, VTP, CDP, DTP, PagP, or LACP).
•A destination port that belongs to a source VLAN of any SPAN session is excluded from the source list and is not monitored.
•No address learning occurs on the destination port.
Now that we have the sessions set up:
We can now start Wireshark on SVR and monitor the traffic of PCC. You can see based on the Filter expression, I’m filtering out stp and hsrp packets that are being propagated on DLS2’s fa0/18 link. I also enabled bpdu filter on DLS1 fa0/6 interface (to SRV) to help reduce the packets showing up in Wireshark.
The following shows a ping from PCB to PCC which SRV is monitoring via RSPAN:
Ping Capture on SRV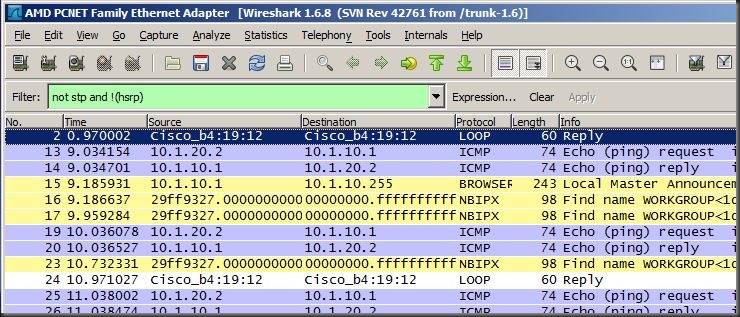
And here we can see PCB (10.1.20.2) is sending an ICMP (ping) request to PCC (10.1.10.1) and Wireshark running on SRV is capturing the packets.
-Prost!
(1) http://www.cisco.com/en/US/docs/switches/lan/catalyst3550/software/release/12.1_13_ea1/configuration/guide/swspan.html#wp1036740


No comments:
Post a Comment