Part 1: Configuring the Radius Server
In this post we want to secure access to our devices and do so with a single authentication server. There are many reasons to do this; for example we can easily manage users and passwords without having to micromanage each device.
The topology is similar to the RSPAN post:
DLS1 VLAN 5 (MGT): 10.1.5.252
DLS2 VLAN 5 (MGT): 10.1.5.253
We will be hosting WinRadius on SRV which will authenticate access to devices DLS1 and DLS2. We will access DLS1 & DLS2 via PCB using telnet and the MGT VLAN.
To speed things up all devices can ping each other and the network is converged. Let’s get started…
I’m using WinRadius because it’s used in the CCNP curriculum. You can find the free version online; there are other free Radius programs available but I am only going to use WinRadius for this post. Also note that RADIUS isn’t as secure as TACACS+ but TACACS+ is Cisco proprietary and the configuration is beyond this scope.
If you’ve decided not to follow along with a WinRadius setup then you can skip to Part 2.
After you’ve downloaded the WinRadius zip file (and un-zipped it) you will notice that there two executable files.
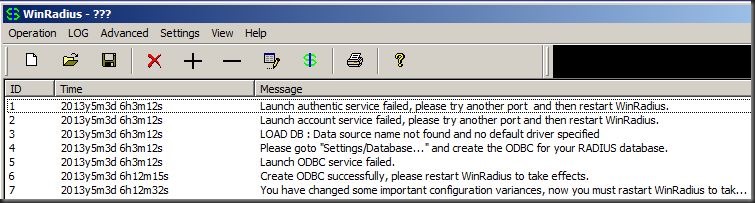
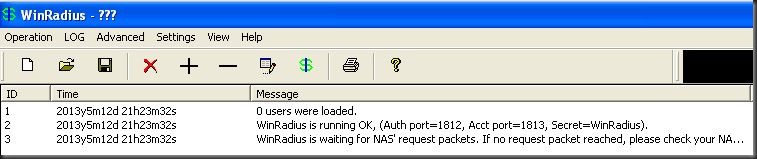
WinRadius runs in its own instance so there isn’t anything to install. When you first run the WinRadius.exe file you will get an error (or list of errors) that say something to the fact that “Launch ODBC service failed”.
ID 1: Launch authentic service failed, please try another port and then restart WinRadius.
ID 2: Launch account service failed, please try another port and then restart winRadius
In my case the first two messages indicate that port 1812 for Authorization and 1813 port for Accounting are being used by another service on SVR. I will need to change these port numbers by going to Settings > System
Take note of the NAS Secret password, the RADIUS IP, and the port numbers. We will need these later. I’ve changed the Authorization port to 2812 and the Accounting port to 2813. I won’t know if those ports are available until after I restart WinRadius. But before I do…
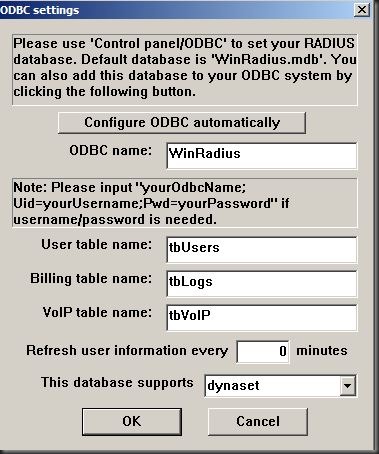
The ODBC needs to be configured and this can be done automatically. Go to Settings > Database …
Click on “Configure ODBC Automatically” and click “OK”….
The main WinRadius window should now have a couple extra logs:
ID 6: Create ODBC successfully, please restart WinRadius to take effect
ID 7: You have changed some important configuration variances, now you must restart WinRadius…
Close out and then re-run WinRadius.exe again.
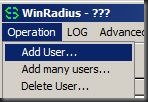
We now want to configure User names and Passwords. The version I have (free) supports 5 users but we will only be configuring one. Go to Operation > Add user:
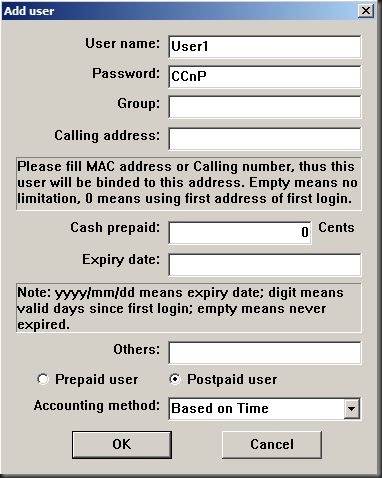
Here you can be creative and make up your own names and passwords. Keep your user names below 8 characters in length as the test server we will use has a limitation. After you configure the user name & password, click “OK” and you should see a log message in WinRadius informing you of success (“Add user successfully”). For added security, if the “User” has a static IP you could add this to the Calling address (???). Since I have dhcp setup on PCB I’m not going to use this.
User name: User1
Password: CCnP
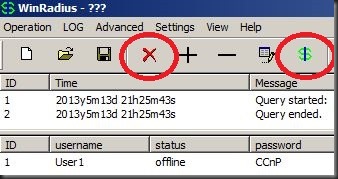
The red “X” in the tool bar can be used to clear the log screen. Also, the green “$” is a query and will show you your users:
Now, to test the server and our user…
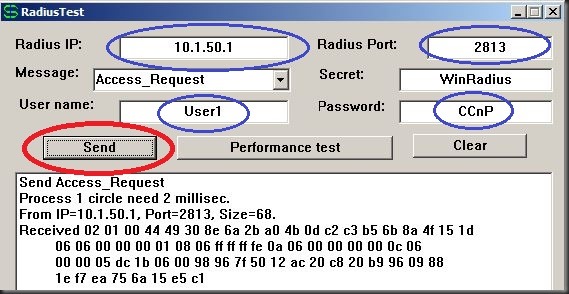
In the WinRadius folder you should find a second executable file called RadiusTest.exe. We want to run this to make sure we have the user name, password, IP and port number correct.
Here you can see I set the Radius IP (SRV: 10.1.50.1), changed the port to reflect 2813 (since 1813 wasn’t available), put in the username and password then clicked “Send”. You should see some feedback within a few seconds, if not then you will need to recheck your port numbers and configuration. The “Secret:” field should be left at the default unless you’ve changed it.
Back on the main WinRadius window you will see a log message:
ID 3: User (User1) authenticate OK.
Now we need to configure the switches DLS1 & DLS2… (See Part 2)


![clip_image001[1] clip_image001[1]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgy-9igaisewnhAb7P3h64rEM-Npj-uxfcCabAK3ARTFmTskaOLkXoblb0njEahQyO549qi6bRX8nbb8mOK1bpxUoIAB_p9uHXYsaXL3BqI_jES3PWNptwEVY5L1J0eT4-j9aMZ4nOJ66k/?imgmax=800)




No comments:
Post a Comment